CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
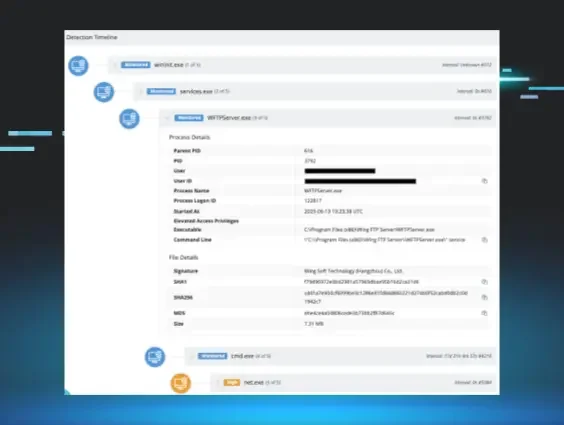
🚨 Marked as known exploited on July 10th, 2025 (1 day ago).
Description: Huntress discovered active exploitation of Wing FTP Server RCE (CVE-2025-47812). Learn more about the injection flaw, attack timeline, forensic artifacts, and how to protect your organization.
EPSS Score: 57.3%
July 10th, 2025 (1 day ago)
|

|
Description: George Allen Construction specializes in providing innovative solutions for railroad construction projects,
catering to the un...
July 10th, 2025 (1 day ago)
|

|
Description: "For over 35 years Wheels Automotive Dealer Supplies has been Canada’s leader in Automotive retail products - as a manufacturer,...
July 10th, 2025 (1 day ago)
|
|
CVE-2025-7425 |
Description: A flaw was found in libxslt where the attribute type, atype, flags are modified in a way that corrupts internal memory management. When XSLT functions, such as the key() process, result in tree fragments, this corruption prevents the proper cleanup of ID attributes. As a result, the system may access freed memory, causing crashes or enabling attackers to trigger heap corruption.
EPSS Score: 0.01%
July 10th, 2025 (1 day ago)
|
|
CVE-2024-36697 |
Description: A cross-site scripting (XSS) vulnerability in the Admin Login page of Allworx System Software v9.1.9.12 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the SessionID parameter at query.asp.
EPSS Score: 0.03%
July 10th, 2025 (1 day ago)
|

|
Description: Daniil Kasatkin, 26, was detained in June at Paris’s Charles de Gaulle Airport shortly after arriving in the country with his fiancée, according to local media reports.
July 10th, 2025 (1 day ago)
|

|
Description: FBI's Criminal Justice Information Services (CJIS) compliance isn't optional when handling law enforcement data. From MFA to password hygiene, see how Specops Software helps meet FBI standards while also securing your Windows Active Directory. [...]
July 10th, 2025 (2 days ago)
|

|
Description: The AIs are designed to teach people about atrocities in Sudan.
July 10th, 2025 (2 days ago)
|
|
Description: “If such a force is observed, it would be an incredible breakthrough in physics,” said one researcher.
July 10th, 2025 (2 days ago)
|

|
Description: In 2025, US-based violent extremists are likely to favor targeted attacks over mass-casualty events. Explore threat forecasts, ideological trends, and countermeasures in this Insikt Group intelligence report.
July 10th, 2025 (2 days ago)
|
