Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Cybersecurity researchers are warning about a large-scale phishing campaign targeting WooCommerce users with a fake security alert urging them to download a "critical patch" but deploy a backdoor instead.
WordPress security company Patchstack described the activity as sophisticated and a variant of another campaign observed in December 2023 that employed a fake CVE ploy to breach sites running
April 28th, 2025 (about 1 month ago)
|
|
CVE-2025-0627 |
Description: The WordPress Tag, Category, and Taxonomy Manager WordPress plugin before 3.30.0 does not sanitise and escape some of its Widgets settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup).
EPSS Score: 0.03%
April 28th, 2025 (about 1 month ago)
|
|
CVE-2024-9771 |
Description: The WP-Recall WordPress plugin before 16.26.12 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup).
EPSS Score: 0.03%
April 28th, 2025 (about 1 month ago)
|

|
Description: A large-scale phishing campaign targets WooCommerce users with a fake security alert urging them to download a "critical patch" that adds a Wordpress backdoor to the site. [...]
April 27th, 2025 (about 1 month ago)
|
|
CVE-2025-0671 |
Description: The Icegram Express WordPress plugin before 5.7.50 does not sanitise and escape some of its Template settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup).
EPSS Score: 0.03%
April 25th, 2025 (about 1 month ago)
|
|
CVE-2025-2558 |
Description: The-wound WordPress theme through 0.0.1 does not validate some parameters before using them to generate paths passed to include function/s, allowing unauthenticated users to perform LFI attacks and download arbitrary file from the server
EPSS Score: 0.08%
April 24th, 2025 (about 1 month ago)
|
|
CVE-2025-1453 |
Description: The Category Posts Widget WordPress plugin before 4.9.20 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup).
EPSS Score: 0.03%
April 24th, 2025 (about 1 month ago)
|

|
Description: The Patchstack team has been monitoring a large-scale phishing campaign using a sophisticated email and web-based phishing template to warn users of a supposed security vulnerability in their WooCommerce installation. This attack bears a very striking similarity to a phishing campaign we reported on previously, this time targeting WooCommerce users specifically, instead of WordPress users […]
The post Fake Security Vulnerability Phishing Campaign Targets WooCommerce Users appeared first on Patchstack.
April 23rd, 2025 (about 1 month ago)
|
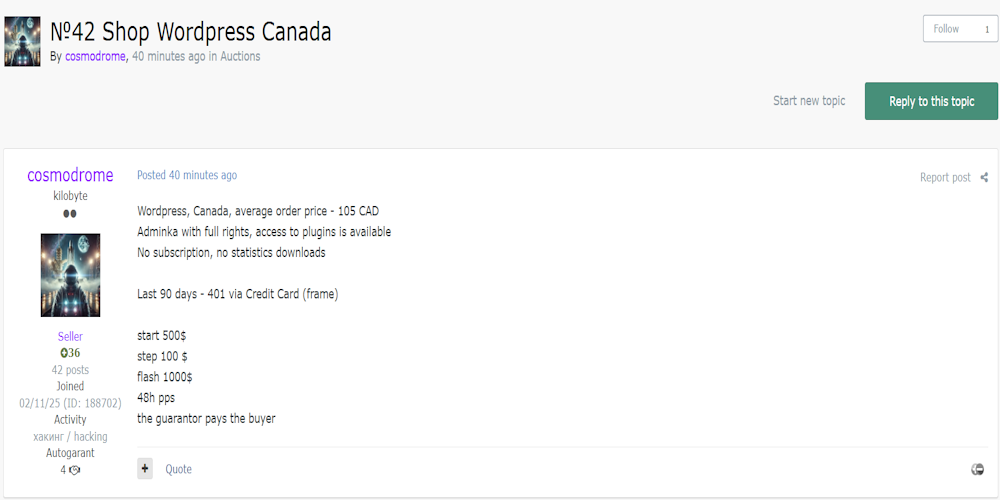
|
Description: Alleged Unauthorized Access to WordPress eCommerce Site of an Unnamed Canadian Retail Store Listed for Sale
April 22nd, 2025 (about 1 month ago)
|
|
CVE-2025-2594 |
Description: The User Registration & Membership WordPress plugin before 4.1.3 does not properly validate data in an AJAX action when the Membership Addon is enabled, allowing attackers to authenticate as any user, including administrators, by simply using the target account's user ID.
EPSS Score: 0.05%
April 22nd, 2025 (about 2 months ago)
|
