Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
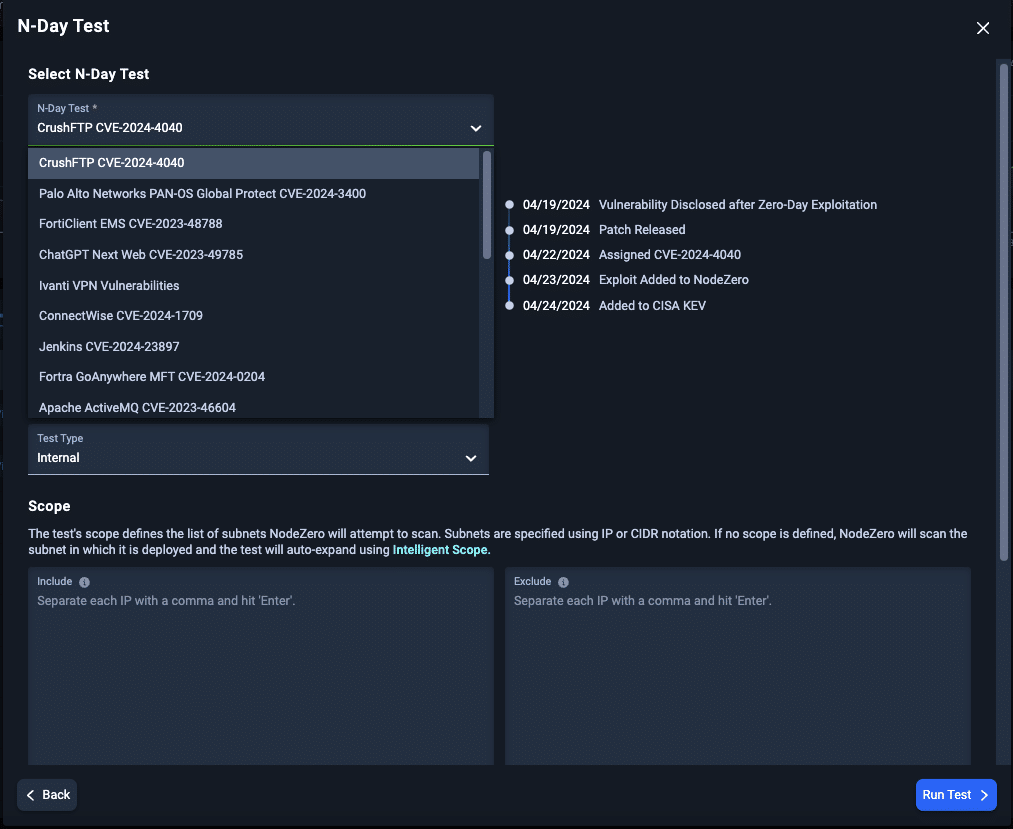
|
Description: Cisco IOS XE Wireless Controller Software Arbitrary File Upload Vulnerability
CVSS: CRITICAL (10.0) EPSS Score: 3.8%
May 30th, 2025 (7 days ago)
|
|
CVE-2024-23771 |
Description: darkhttpd before 1.15 uses strcmp (which is not constant time) to verify authentication, which makes it easier for remote attackers to bypass authentication via a timing side channel.
CVSS: CRITICAL (9.8) EPSS Score: 0.24% SSVC Exploitation: none
May 30th, 2025 (7 days ago)
|
|
CVE-2024-23752 |
Description: GenerateSDFPipeline in synthetic_dataframe in PandasAI (aka pandas-ai) through 1.5.17 allows attackers to trigger the generation of arbitrary Python code that is executed by SDFCodeExecutor. An attacker can create a dataframe that provides an English language specification of this Python code. NOTE: the vendor previously attempted to restrict code execution in response to a separate issue, CVE-2023-39660.
CVSS: CRITICAL (9.8) EPSS Score: 0.51% SSVC Exploitation: poc
May 30th, 2025 (7 days ago)
|
|
CVE-2024-23730 |
Description: The OpenAPI and ChatGPT plugin loaders in LlamaHub (aka llama-hub) before 0.0.67 allow attackers to execute arbitrary code because safe_load is not used for YAML.
CVSS: CRITICAL (9.8) EPSS Score: 0.14% SSVC Exploitation: none
May 30th, 2025 (7 days ago)
|
|
CVE-2024-22663 |
Description: TOTOLINK_A3700R_V9.1.2u.6165_20211012has a command Injection vulnerability via setOpModeCfg
CVSS: CRITICAL (9.8) EPSS Score: 3.56% SSVC Exploitation: poc
May 30th, 2025 (7 days ago)
|
|
CVE-2025-2500 |
Description: A vulnerability exists in the SOAP Web services of the Asset
Suite versions listed below. If successfully exploited, an attacker
could gain unauthorized access to the product and the time window of a possible password attack could be expanded.
CVSS: CRITICAL (9.1) EPSS Score: 0.05%
May 30th, 2025 (8 days ago)
|
|
CVE-2025-48865 |
Description: Fabio is an HTTP(S) and TCP router for deploying applications managed by consul. Prior to version 1.6.6, Fabio allows clients to remove X-Forwarded headers (except X-Forwarded-For) due to a vulnerability in how it processes hop-by-hop headers. Fabio adds HTTP headers like X-Forwarded-Host and X-Forwarded-Port when routing requests to backend applications. Since the receiving application should trust these headers, allowing HTTP clients to remove or modify them creates potential security vulnerabilities. Some of these custom headers can be removed and, in certain cases, manipulated. The attack relies on the behavior that headers can be defined as hop-by-hop via the HTTP Connection header. This issue has been patched in version 1.6.6.
CVSS: CRITICAL (9.1) EPSS Score: 0.02%
May 30th, 2025 (8 days ago)
|
|
CVE-2025-48757 |
Description: An insufficient database Row-Level Security policy in Lovable through 2025-04-15 allows remote unauthenticated attackers to read or write to arbitrary database tables of generated sites.
CVSS: CRITICAL (9.3) EPSS Score: 0.04%
May 30th, 2025 (8 days ago)
|
|
CVE-2025-46352 |
Description: The CS5000 Fire Panel is vulnerable due to a hard-coded password that
runs on a VNC server and is visible as a string in the binary
responsible for running VNC. This password cannot be altered, allowing
anyone with knowledge of it to gain remote access to the panel. Such
access could enable an attacker to operate the panel remotely,
potentially putting the fire panel into a non-functional state and
causing serious safety issues.
CVSS: CRITICAL (9.8) EPSS Score: 0.05%
May 30th, 2025 (8 days ago)
|
|
CVE-2025-41438 |
Description: The CS5000 Fire Panel is vulnerable due to a default account that exists
on the panel. Even though it is possible to change this by SSHing into
the device, it has remained unchanged on every installed system
observed. This account is not root but holds high-level permissions that
could severely impact the device's operation if exploited.
CVSS: CRITICAL (9.8) EPSS Score: 0.06%
May 30th, 2025 (8 days ago)
|
