CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
🚨 Marked as known exploited on July 10th, 2025 (about 19 hours ago).
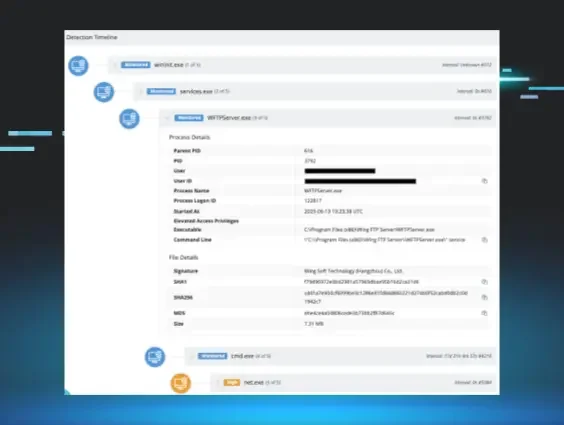
Description: Huntress discovered active exploitation of Wing FTP Server RCE (CVE-2025-47812). Learn more about the injection flaw, attack timeline, forensic artifacts, and how to protect your organization.
July 10th, 2025 (about 19 hours ago)
|

|
🚨 Marked as known exploited on July 8th, 2025 (3 days ago).
Description: Ivanti releases standard security patches on the second Tuesday of every month. Our vulnerability management program is central to our commitment to maintaining secure products. Our philosophy is simple: discovering and communicating vulnerabilities, and sharing that information with defenders, is not an indication of weakness; rather it is evidence of rigorous scrutiny and a proactive vulnerability management program. By aggressively seeking to identify and address vulnerabilities, our aim is to get ahead of threat actors to ensure our customers can take the steps needed to protect their environments. At the core, we believe that responsible transparency helps protect our customers.
We believe that responsible transparency helps protect our customers, and that CVE disclosures are an essential and effective tool to communicate software vulnerabilities. The purpose of assigning a CVE is to provide a beacon to security teams and signal the need for urgent updates.
To that end, today Ivanti is disclosing vulnerabilities in Ivanti Connect Secure and Policy Secure, Ivanti EPM, and Ivanti EPMM.
It is important for customers to know:
We have no evidence of any of these vulnerabilities being exploited in the wild.
These vulnerabilities do not impact any other Ivanti solutions.
More information on these vulnerabilities and detailed instructions on how to remediate the issues can be found in these Security Advisories:
Ivanti Connect Secure and Policy Secure
Ivanti EP...
July 8th, 2025 (3 days ago)
|

|
🚨 Marked as known exploited on July 8th, 2025 (3 days ago).
Description: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added four security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild.
The list of flaws is as follows -
CVE-2014-3931 (CVSS score: 9.8) - A buffer overflow vulnerability in Multi-Router Looking Glass (MRLG) that could allow remote attackers to cause an
CVSS: CRITICAL (9.8)
July 8th, 2025 (3 days ago)
|
|
CVE-2014-3931 |
🚨 Marked as known exploited on July 7th, 2025 (4 days ago).
Description: CISA has added four new vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, based on evidence of active exploitation.
CVE-2014-3931 Multi-Router Looking Glass (MRLG) Buffer Overflow Vulnerability
CVE-2016-10033 PHPMailer Command Injection Vulnerability
CVE-2019-5418 Rails Ruby on Rails Path Traversal Vulnerability
CVE-2019-9621 Synacor Zimbra Collaboration Suite (ZCS) Server-Side Request Forgery (SSRF) Vulnerability
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the KEV Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise. BOD 22-01 requires Federal Civilian Executive Branch (FCEB) agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of KEV Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the catalog that meet the specified criteria.
CVSS: CRITICAL (9.8)
July 7th, 2025 (4 days ago)
|
|
CVE-2025-6554 |
🚨 Marked as known exploited on July 2nd, 2025 (9 days ago).
Description: CISA has added one new vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog, based on evidence of active exploitation.
CVE-2025-6554 Google Chromium V8 Type Confusion Vulnerability
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the KEV Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise. BOD 22-01 requires Federal Civilian Executive Branch (FCEB) agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of KEV Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the catalog that meet the specified criteria.
EPSS Score: 5.3%
July 2nd, 2025 (9 days ago)
|

|
🚨 Marked as known exploited on July 1st, 2025 (10 days ago).
Description: Google has released emergency updates to patch another Chrome zero-day vulnerability exploited in attacks, marking the fourth such flaw fixed since the start of the year. [...]
July 1st, 2025 (10 days ago)
|

|
🚨 Marked as known exploited on July 1st, 2025 (10 days ago).
Description: Google has released security updates to address a vulnerability in its Chrome browser for which an exploit exists in the wild.
The zero-day vulnerability, tracked as CVE-2025-6554 (CVSS score: N/A), has been described as a type confusing flaw in the V8 JavaScript and WebAssembly engine.
"Type confusion in V8 in Google Chrome prior to 138.0.7204.96 allowed a remote attacker to perform arbitrary
EPSS Score: 5.3%
July 1st, 2025 (10 days ago)
|

|
🚨 Marked as known exploited on July 1st, 2025 (10 days ago).
Description: Google has shipped a security update for Chrome addressing a high-severity vulnerability in the V8 JavaScript engine that is already being exploited in the wild. Tracked as CVE-2025-6554, the flaw is categorized as a type confusion issue in V8 and was reported on June 25, 2025, by Clément Lecigne of Google’s Threat Analysis Group (TAG). …
The post Google Patches Actively Exploited V8 Vulnerability in Chrome appeared first on CyberInsider.
EPSS Score: 5.3%
July 1st, 2025 (10 days ago)
|
|
CVE-2025-6554 |
🚨 Marked as known exploited on July 1st, 2025 (10 days ago).
Description: Type confusion in V8 in Google Chrome prior to 138.0.7204.96 allowed a remote attacker to perform arbitrary read/write via a crafted HTML page. (Chromium security severity: High)
EPSS Score: 5.3%
June 30th, 2025 (10 days ago)
|

|
🚨 Marked as known exploited on June 30th, 2025 (11 days ago).
Description: Over 1,200 Citrix NetScaler ADC and NetScaler Gateway appliances exposed online are unpatched against a critical vulnerability believed to be actively exploited, allowing threat actors to bypass authentication by hijacking user sessions. [...]
June 30th, 2025 (11 days ago)
|
