CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: The campaign has affected hundreds of Russian users, particularly targeting industrial enterprises and engineering schools, with additional victims reported in Belarus and Kazakhstan.
June 10th, 2025 (3 days ago)
|

|
Description: The threat actor known as Rare Werewolf (formerly Rare Wolf) has been linked to a series of cyber attacks targeting Russia and the Commonwealth of Independent States (CIS) countries.
"A distinctive feature of this threat is that the attackers favor using legitimate third-party software over developing their own malicious binaries," Kaspersky said. "The malicious functionality of the campaign
June 10th, 2025 (3 days ago)
|

|
Description: Russia's Federal Security Service (FSB) has reportedly intercepted private messages between Russian citizens and Ukrainian Telegram channel bots, initiating treason investigations based on the contents, according to human rights NGO First Department. The revelation underscores escalating digital surveillance and raises concerns about Telegram's security posture amid Russia's deepening crackdown on dissent. Shades on Telegram The …
The post Russian NGO Warns the FSB Is Intercepting Telegram Messages to Prosecute Users appeared first on CyberInsider.
June 10th, 2025 (3 days ago)
|

|
Description: In its latest campaign this spring, DarkGaboon was observed deploying LockBit 3.0 ransomware against victims in Russia, Positive Technologies said in a report last week.
June 9th, 2025 (4 days ago)
|

|
Description: OpenAI has revealed that it banned a set of ChatGPT accounts that were likely operated by Russian-speaking threat actors and two Chinese nation-state hacking groups to assist with malware development, social media automation, and research about U.S. satellite communications technologies, among other things.
"The [Russian-speaking] actor used our models to assist with developing and refining
June 9th, 2025 (4 days ago)
|

|
June 6th, 2025 (7 days ago)
|
|
Description: The new PathWiper, spotted in an attack on Ukrainian critical infrastructure, has similarities to wiper malware previously deployed by the Russian group known as Sandworm.
June 6th, 2025 (7 days ago)
|
|
June 5th, 2025 (7 days ago)
|

|
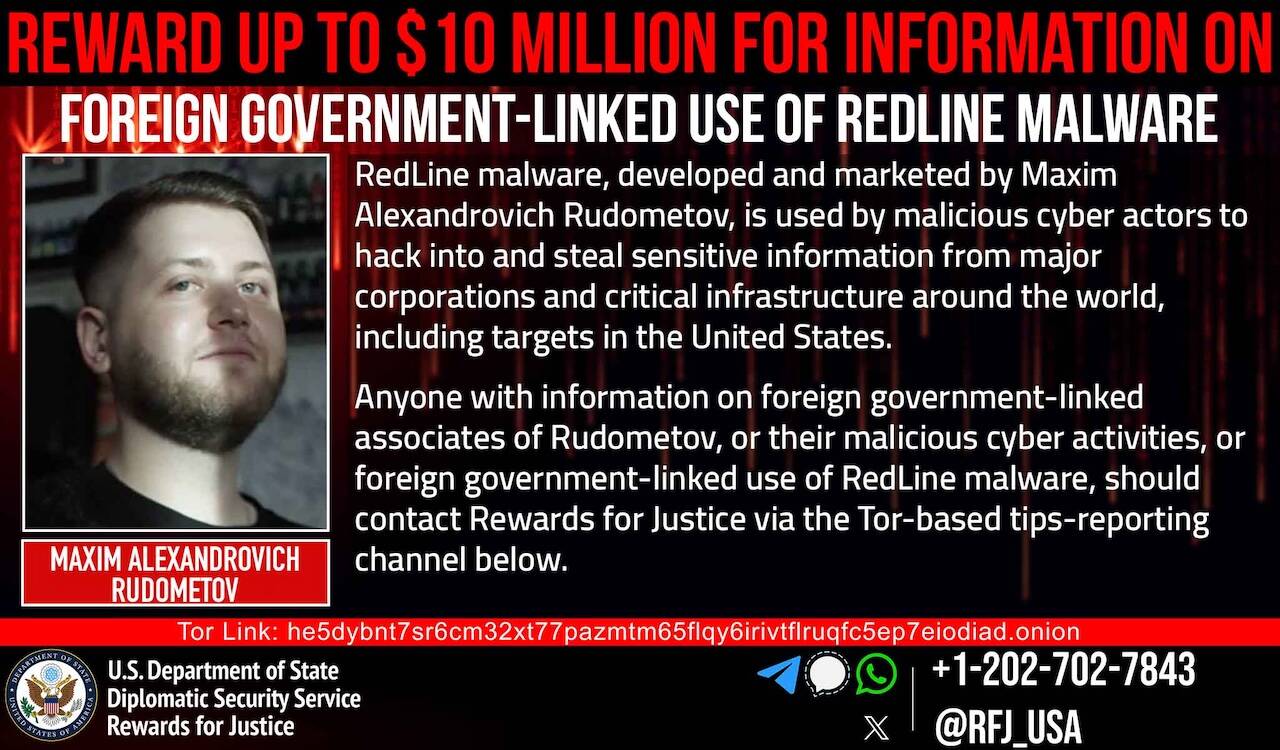
Description: The U.S. Department of State has announced a reward of up to $10 million for any information on government-sponsored hackers with ties to the RedLine infostealer malware operation and its suspected creator, Russian national Maxim Alexandrovich Rudometov. [...]
June 5th, 2025 (8 days ago)
|

|
June 4th, 2025 (8 days ago)
|
