CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
🚨 Marked as known exploited on July 16th, 2025 (about 17 hours ago).
Description: Google has released a security update for Chrome to address half a dozen vulnerabilities, one of them actively exploited by attackers to escape the browser's sandbox protection. [...]
July 16th, 2025 (about 17 hours ago)
|

|
🚨 Marked as known exploited on July 16th, 2025 (about 18 hours ago).
Description: Google on Tuesday rolled out fixes for six security issues in its Chrome web browser, including one that it said has been exploited in the wild.
The high-severity vulnerability in question is CVE-2025-6558 (CVSS score: 8.8), which has been described as an incorrect validation of untrusted input in the browser's ANGLE and GPU components.
"Insufficient validation of untrusted input in ANGLE and
July 16th, 2025 (about 18 hours ago)
|

|
🚨 Marked as known exploited on July 16th, 2025 (about 19 hours ago).
Description: Google has released an emergency security update for Chrome, addressing six vulnerabilities, including a high-severity flaw currently exploited in the wild. The actively targeted issue, tracked as CVE-2025-6558, stems from improper validation of untrusted input in Chrome's ANGLE and GPU components. The vulnerability was discovered and reported by Clément Lecigne and Vlad Stolyarov of Google's …
The post Google Patches Actively Exploited Sandbox Escape Flaw in Chrome appeared first on CyberInsider.
July 16th, 2025 (about 19 hours ago)
|
|
CVE-2025-6558 |
🚨 Marked as known exploited on July 16th, 2025 (about 19 hours ago).
Description: Insufficient validation of untrusted input in ANGLE and GPU in Google Chrome prior to 138.0.7204.157 allowed a remote attacker to potentially perform a sandbox escape via a crafted HTML page. (Chromium security severity: High)
SSVC Exploitation: none
July 15th, 2025 (1 day ago)
|

|
🚨 Marked as known exploited on July 14th, 2025 (2 days ago).
Description: A critical vulnerability in products from the file transfer company Wing FTP Server is being actively exploited, the Cybersecurity and Infrastructure Security Agency said.
July 14th, 2025 (2 days ago)
|

|
🚨 Marked as known exploited on July 14th, 2025 (3 days ago).
Description: Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this post, we answer some questions we’ve gotten recently about the best way to determine, understand and communicate your risks. You can read the entire Exposure Management Academy series here.The Exposure Management Academy receives lots of questions from readers — some who are already running an exposure management program and some who are considering it. In previous FAQs, we’ve dealt with a number of topics that are top-of-mind for security leaders and practitioners. This time, we thought we’d focus on questions around what you need to launch a unified security program with an exposure management approach.How do I start getting a clear picture of all my cyber risks? My data is everywhere!You’re not alone in asking this question. It’s a common challenge for organizations just starting with exposure management. You’ve probably built your IT environment over years, if not decades, and it includes a wide array of platforms. Maybe you have on-premises infrastructure, a bunch of cloud environments, containerized applications, web applications and operational technology. It’s a near certainty that each of those elements of your infrastructure has squirreled away insights about your overall cyber vulnerabilities. And because they’re not connected, you can’t assess that information in the context of your over...
July 14th, 2025 (3 days ago)
|
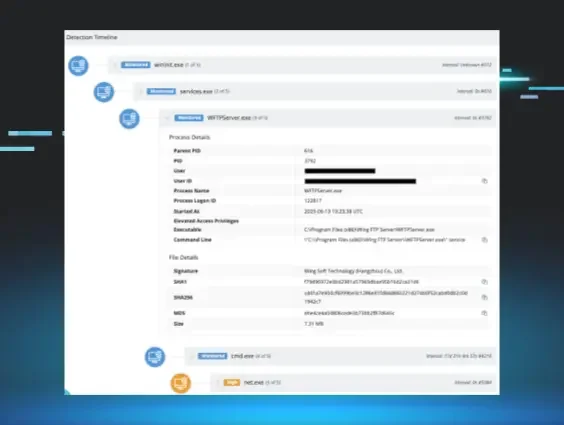
|
🚨 Marked as known exploited on July 10th, 2025 (7 days ago).
Description: Huntress discovered active exploitation of Wing FTP Server RCE (CVE-2025-47812). Learn more about the injection flaw, attack timeline, forensic artifacts, and how to protect your organization.
EPSS Score: 83.43%
July 10th, 2025 (7 days ago)
|

|
🚨 Marked as known exploited on July 8th, 2025 (9 days ago).
Description: Ivanti releases standard security patches on the second Tuesday of every month. Our vulnerability management program is central to our commitment to maintaining secure products. Our philosophy is simple: discovering and communicating vulnerabilities, and sharing that information with defenders, is not an indication of weakness; rather it is evidence of rigorous scrutiny and a proactive vulnerability management program. By aggressively seeking to identify and address vulnerabilities, our aim is to get ahead of threat actors to ensure our customers can take the steps needed to protect their environments. At the core, we believe that responsible transparency helps protect our customers.
We believe that responsible transparency helps protect our customers, and that CVE disclosures are an essential and effective tool to communicate software vulnerabilities. The purpose of assigning a CVE is to provide a beacon to security teams and signal the need for urgent updates.
To that end, today Ivanti is disclosing vulnerabilities in Ivanti Connect Secure and Policy Secure, Ivanti EPM, and Ivanti EPMM.
It is important for customers to know:
We have no evidence of any of these vulnerabilities being exploited in the wild.
These vulnerabilities do not impact any other Ivanti solutions.
More information on these vulnerabilities and detailed instructions on how to remediate the issues can be found in these Security Advisories:
Ivanti Connect Secure and Policy Secure
Ivanti EP...
July 8th, 2025 (9 days ago)
|
|
CVE-2025-6554 |
🚨 Marked as known exploited on July 2nd, 2025 (14 days ago).
Description: CISA has added one new vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog, based on evidence of active exploitation.
CVE-2025-6554 Google Chromium V8 Type Confusion Vulnerability
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the KEV Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise. BOD 22-01 requires Federal Civilian Executive Branch (FCEB) agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of KEV Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the catalog that meet the specified criteria.
EPSS Score: 5.3%
July 2nd, 2025 (14 days ago)
|

|
🚨 Marked as known exploited on July 1st, 2025 (16 days ago).
Description: Google has released emergency updates to patch another Chrome zero-day vulnerability exploited in attacks, marking the fourth such flaw fixed since the start of the year. [...]
July 1st, 2025 (16 days ago)
|
